Secure and resilient networking solutions for embedded systems
For more than four decades, Tuxera has been a key player in data transfer for embedded systems, offering safe and secure connectivity software. We specialize in addressing the rising challenges of digitalization even in the smallest IoT devices through our state-of-the-art TCP/IP networking stack and CryptoCore encryption library.

Tuxera TCP/IP
Optimized for any microcontroller, supporting both IPv4 and IPv6 with minimal resource footprint. Developed to MISRA coding standard.
Tuxera Safe TCP/IP
ISO26262 certifiable, scalable TCP/IP communication stack designed for automotive and expandable to other industries.
CryptoCore™
Comprehensive crypto library with AES, ECDSA, ECDH, SHA-256, and SHA-384, optimized for embedded systems.
Industry applications

Automotive
Automotive ethernet enabling data transmission from Sensors, Radars, Lidars, ECUs, HPCs, ADAS Systems, IVI systems, Telematics, battery monitoring and ethernet backbones.
Why choose Tuxera Networking Stack?
Safety and security
We believe that data safety and security go hand in hand. We follow strict safety standards to ensure every application is secure. We support our customers in thorough risk and hazard assessment processes, HARA and TARA which aids in the certification of the end product. Plus, our reliable TCP/IP stack includes essential security protocols like MACsec, IPsec, and (D)TLS 1.2 and 1.3, making it suitable for use in automotive, industrial, medical, and aerospace fields.
Any hardware, any RTOS, any compiler
Tuxera’s versatile products are compatible with any microcontroller, RTOS, and compiler. These features improves the flexibility to your operations and reduces time-to-market, regardless of hardware changes or performance upgrades.
Resilient and high-quality code
Our TCP/IP and CryptoCore solutions are MISRA compliant and the structure follows the OSI model, ensuring high-quality, secure code that reduces vulnerabilities and cyber-attack risks. Each component undergoes rigorous testing according to TC8 specifications, guaranteeing reliability and performance.
Tuxera Networking Stack architecture diagram
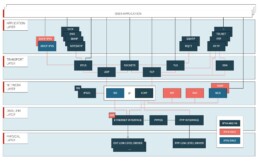
Find more material about our networking stack at the Tuxera Resources page.
Tuxera Networking Stack technical features and modules
Key technical features
- Fully MISRA-compliant
- Supports both IPv4 and IPv6
- Integrates with both RTOS and non-RTOS based systems
- Small RAM and ROM footprint
- High performance
- Multiple network interfaces support
- Extensive set of secure protocols and applications
- Routing module provided
- Native and Sockets interface support
- Wide range of TCP and UDP applications
- Fast/zero copy between network interfaces where common memory pools are defined
- Mechanisms to ensure authenticity, integrity, and confidentiality between devices in a network
Tuxera TCP/IP Stack standard modules
Our TCP/IP stack includes all the standard modules and connectivity features you expect – plus we go above and beyond to provide enhanced features with the following specialized modules. Read more about some of our most-requested TCP/IP modules below.
MQTT
MQTT is a small, low-bandwidth networking protocol ideally suited for connecting embedded applications that are remotely monitored through an internet connection. Tuxera’s MQTT implementation runs on its trusted TCP/IP stack and uses verifiable TLS for secure connections.
NAT
Network Address Translation (NAT) allows an organization to set up a network using private addresses, while still allowing its members to communicate over the public Internet.
SNMP
Tuxera’s SNMP module provides a consistent and reliable way to share information between devices connected on a network. Our high-quality SNMPv2 and SNMPv3 implementation provides embedded devices with secure network management capability. Using SNMP, engineers can monitor device operation and usage, detect network faults or inappropriate access, and configure remote devices. Tuxera’s robust SNMP module is designed for use on a wide variety of network devices, and optimized for minimal impact on managed nodes, low transport overheads, and robust fault tolerance.
Other modules
Physical
Ethernet low-level drivers, PPP Driver
Data link
Ethernet Interface, Serial (PPP) low-level driver
Network
ICMP, IGMP, ARP, AutoIP, ICMP, NAT, ND, MLD, IPv4, IPv6
Transport
UDP, TCP
Session
Sockets
Application
DHCP, DNS, FTP, MQTT, NTP, SMTP, SNTP, Telnet, TFTP, SCP
Secure communications over networks
Our security applications and protocols enable a consistent, secure, and reliable way to share data between embedded devices on a network. Read more about our network security modules below.
EAP
The Extensible Authentication Protocol (EAP) framework is designed to support secure connections for embedded devices. We provide support for many “flavors” of EAP and the framework easily extends to include other protocols. Commonly used algorithms include EAPOL, EAP-TLS, EAP-IKEv2, and EAP-MD5.
EST-CoAP
Enrollment over Secure Transport (EST) is used for authenticated/authorized endpoint certificate enrollment. EST-CoAP uses the Constrained Application Protocol (CoAP) instead of HTTP for Internet of Things (IoT) devices with low-resource environments.
HTTPS Secure Server, HTTPS Secure Client
Our flexible web server solution for embedded systems allows the creation of dynamic content within a highly secure environment. It operates as a request-response protocol in the client/server model. The secure client may be a web browser, while an application hosting a website may be the secure server. HTTPS resources are identified and located on the network using Uniform Resource Identifiers (URIs). HTTPS secure operation relies on Tuxera’s Transport Layer Security (TLS) module.
IPsec and IKE
Our IPSec module ensures integrity, confidentiality, and authentication between two devices in a network. Internet Key Exchange is used by IPsec to set up security associations. Like other components in Tuxera TCP/IP Stack, our IPSec and IKE modules use a strong development process to ensure the modules are reliable and secure.
MACsec
Media Access Control Security (MACsec) provides security on point-to-point Ethernet links or shared Ethernet networks, giving confidentiality, integrity, and authenticity of user data. Our MACsec implementation can be integrated with both RTOS and non-RTOS based systems, is (MCU/CPU) platform independent, and is provided with fully tested reference drivers, plus complete documentation.
SSH (SCP, SFTP)
Tuxera’s Secure Shell (SSH) is a portable, low footprint server that runs as an application on our IPv4 and IPv6 stacks. It creates a secure socket connection that can be used for executing menu commands or for tunneling data between the clients and servers of other applications. The SSH module includes the SSH Authentication, Transport Layer, and Connection Layer protocols. The protocol layers coexist, with each layer supporting multiple simultaneous sessions.
Secure Copy (SCP) and SSH File Transfer Protocol (SFTP) are related secure file transfer protocol modules that use an SSH connection to encrypt passwords and data during transfers.
TLS/DTLS
Our verifiable Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS) is a highly optimized, quality-assured software module designed to provide secure network communications for embedded devices. It provides a framework for secure communication in networks based on the TCP/IP or UDP protocols. Tuxera’s implementation supports TLS 1.0, 1.1, 1.2, and 1.3, and DTLS 1.0, 1.2, and 1.3.
Tuxera CryptoCore™ module for encryption over networks
Our encryption module is a premium add-on to Tuxera TCP/IP Stack, and is necessary to provide secure networking. It allows developers to secure embedded systems using multiple encryption or hash algorithms through a uniform interface. Using a well-defined interface shortens development time, as developers can encrypt data stored on flash or transmitted across a network. Such security is necessary to block potential hackers searching for a backdoor to access embedded system data. Developed using a formal process, Tuxera CryptoCore undergoes verification to ensure stability and enhanced integrity. It is delivered with a full MISRA compliance report. This level of verifiable quality in the area of security and encryption stands in direct contrast with the widely used ‘code-then-test’ methods, which have resulted in serious security breaches. Tuxera CryptoCore provides full certificate management. Available algorithms include AES, 3DES, DSS, ECC, EDH, MD5, RSA, SHA and Tiger.
Read more in the Tuxera TCP/IP Stack overview.
Get Tuxera TCP/IP Stack
For software evaluations, pricing quotes, and more detailed technical specifications, contact us.
What we're talking about
News and updates about embedded file systems
November 14, 2024
What is SMB and why does it matter for file sharing?
November 14, 2024
How to optimize metadata management in Linux file systems
October 17, 2024